Problem
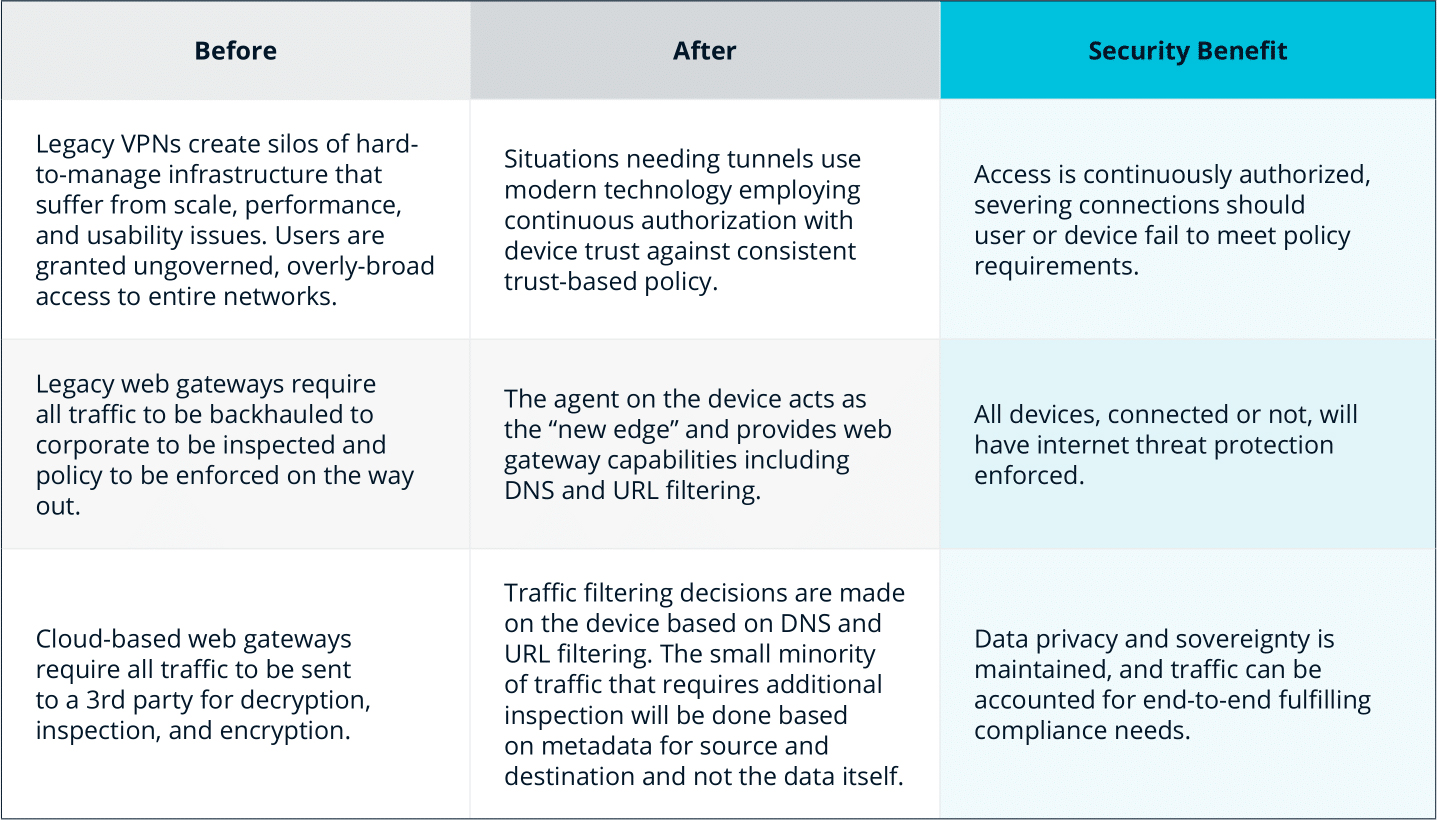
Providing secure zero trust access to applications and infrastructure at scale while protecting the modern workforce from advanced internet threats is challenging. Risk and security must be continuously evaluated, incorporating telemetry from adjacent security tools. With infrastructures growing ever more complex, and applications spread across on-premises, hybrid, and multi-cloud environments, network-centric solutions like legacy VPNs and firewalls have been put to the test and revealed significant performance, usability, and systemic security issues that band-aids cannot fix.
Post-COVID, a significant percentage of workers remain remote, and hiring is now best-in-class, not best-in-geographic region. Increasing reliance on contractors, partners, and other contingent workers makes onboarding, offboarding, and BYOD support critical.
The access and protection strategies that most companies have in place can’t keep up with these realities. A scalable and comprehensive approach is required. A robust Security Service Edge (SSE) solution with ZTNA (Zero Trust Network Access), VPNaaS (VPN as a Service), CASB (Cloud Access Security Broker), and SWG (Secure Web Gateway) components should be evaluated as part of this new strategy.
Use Cases
Modernize Legacy VPN & Firewall
Device Trust and Internet Threat Protection
Support Third-Party Access / BYOD / M&A
Provide third-parties easy, secure access to only specifically needed resources, optionally incorporating device trust. Enable BYOD and protect corporate assets without needing Mobile Device Management (MDM) or Unified Endpoint Management (UEM).
Operational Changes
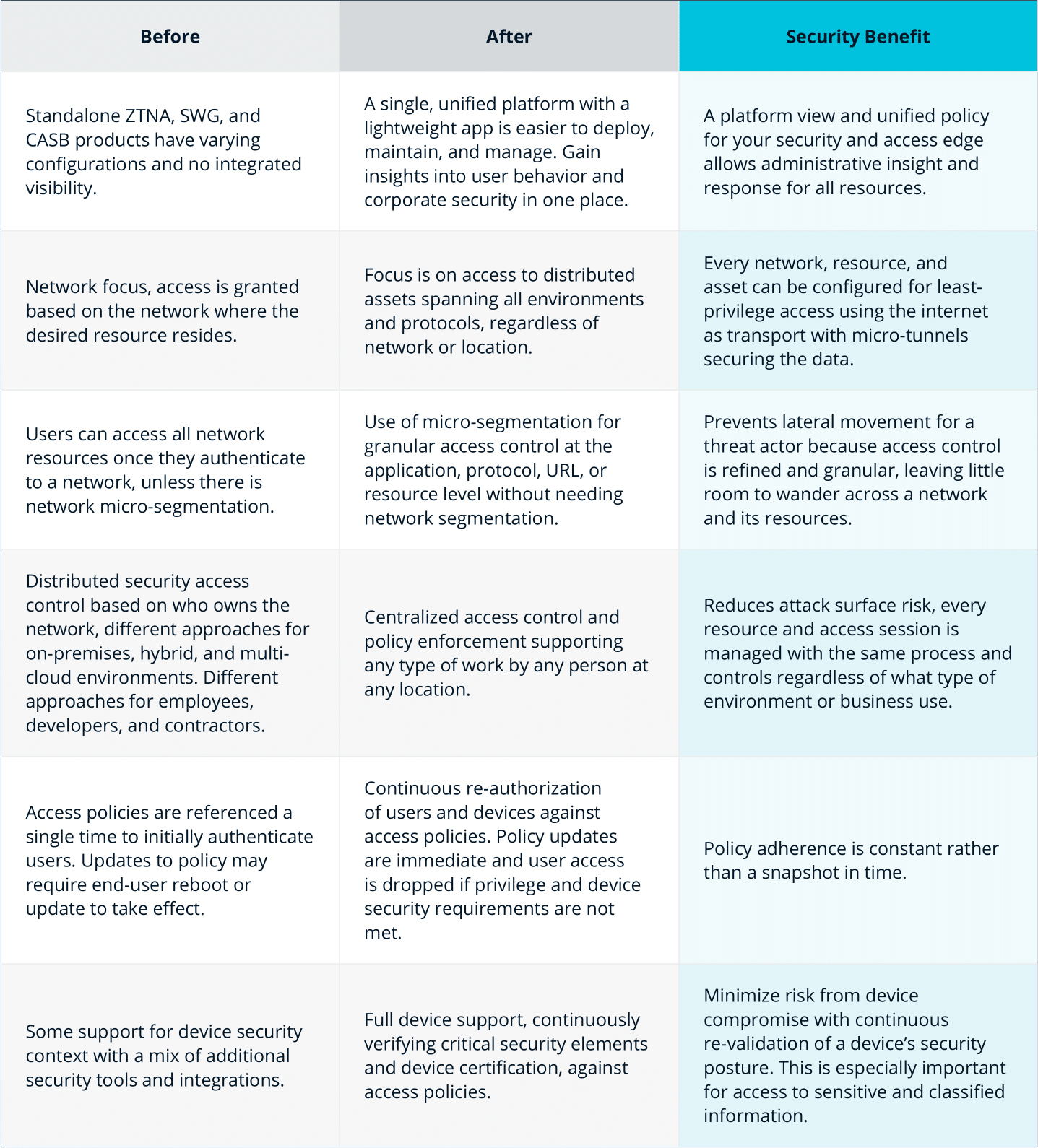
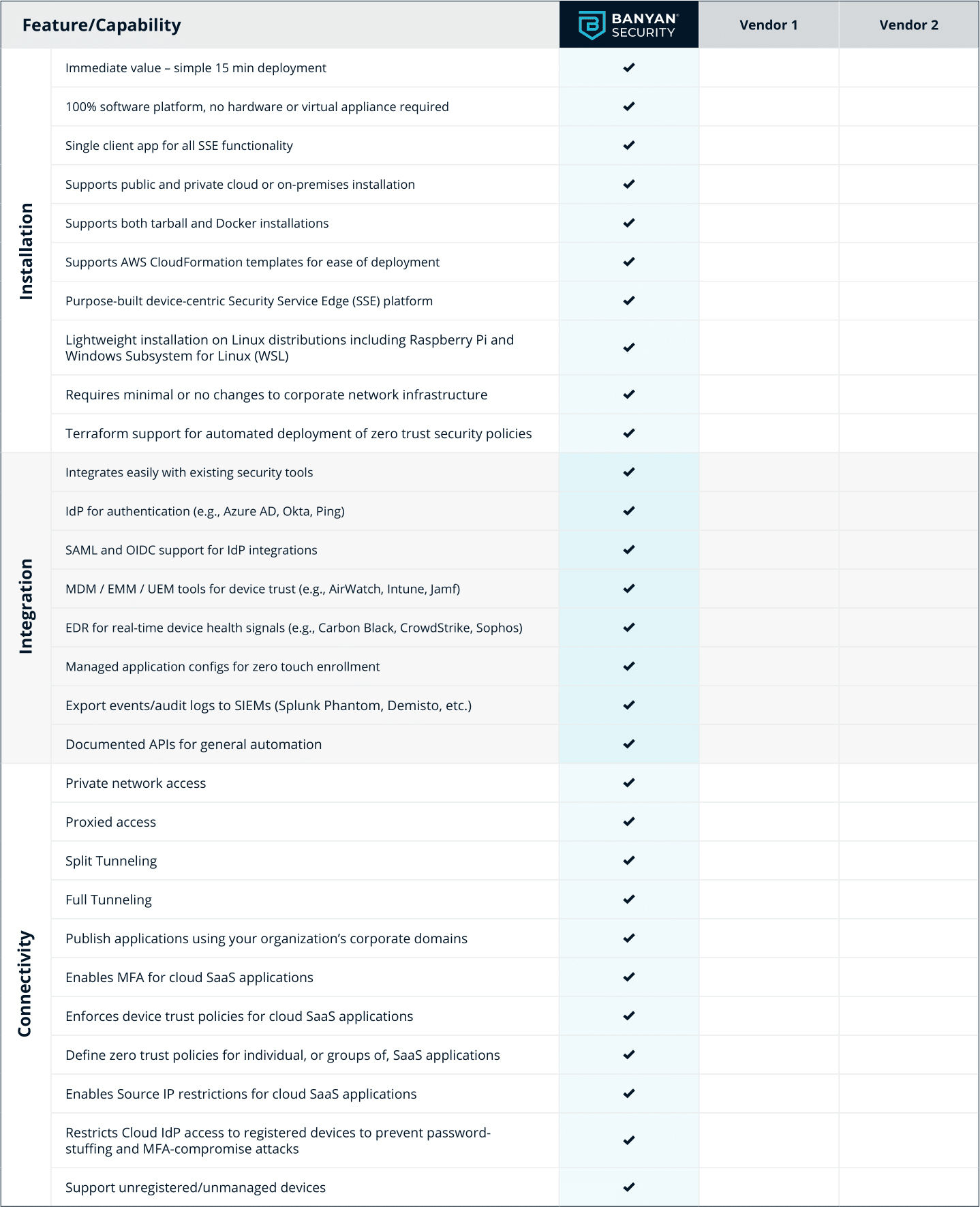
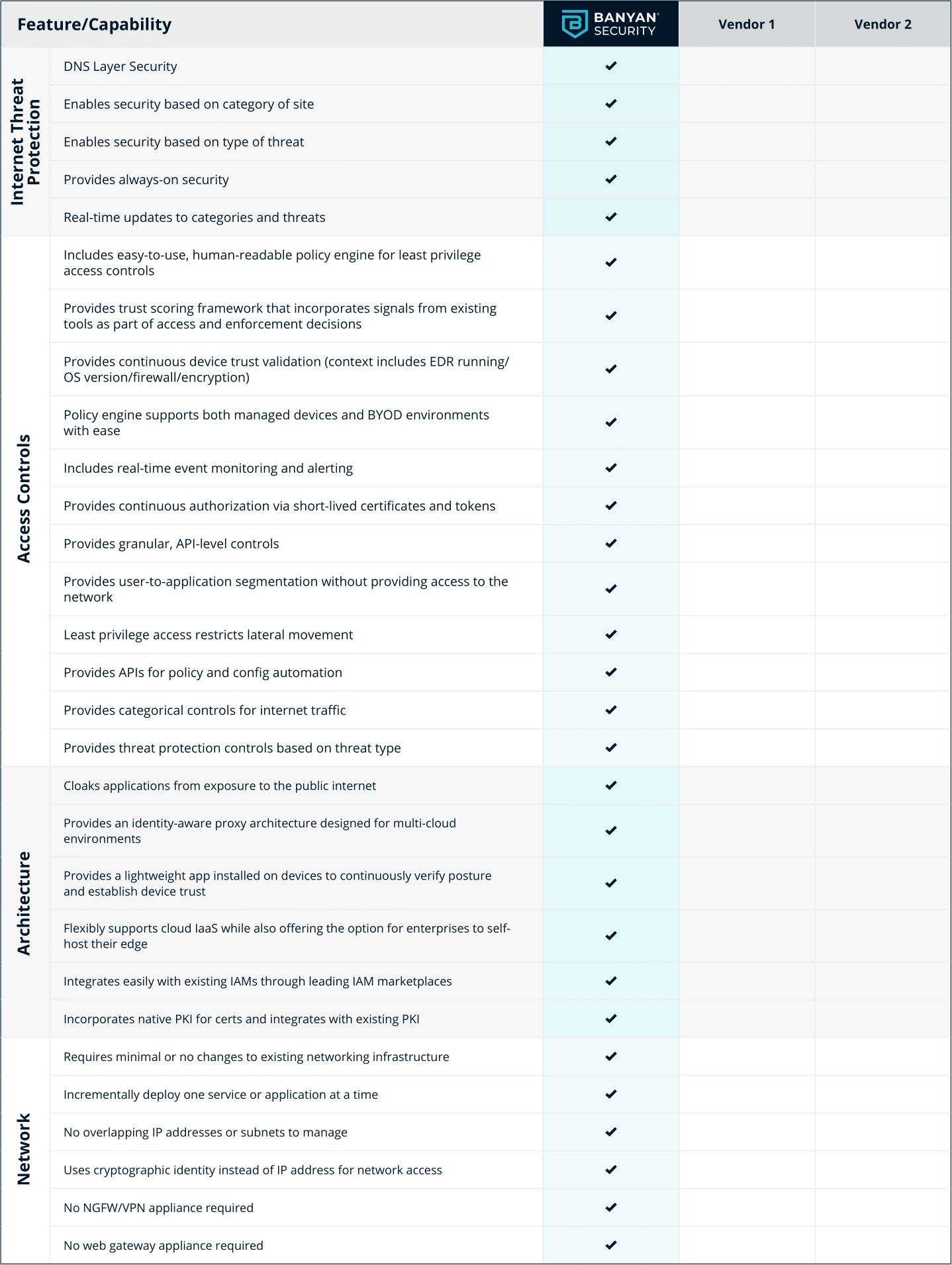
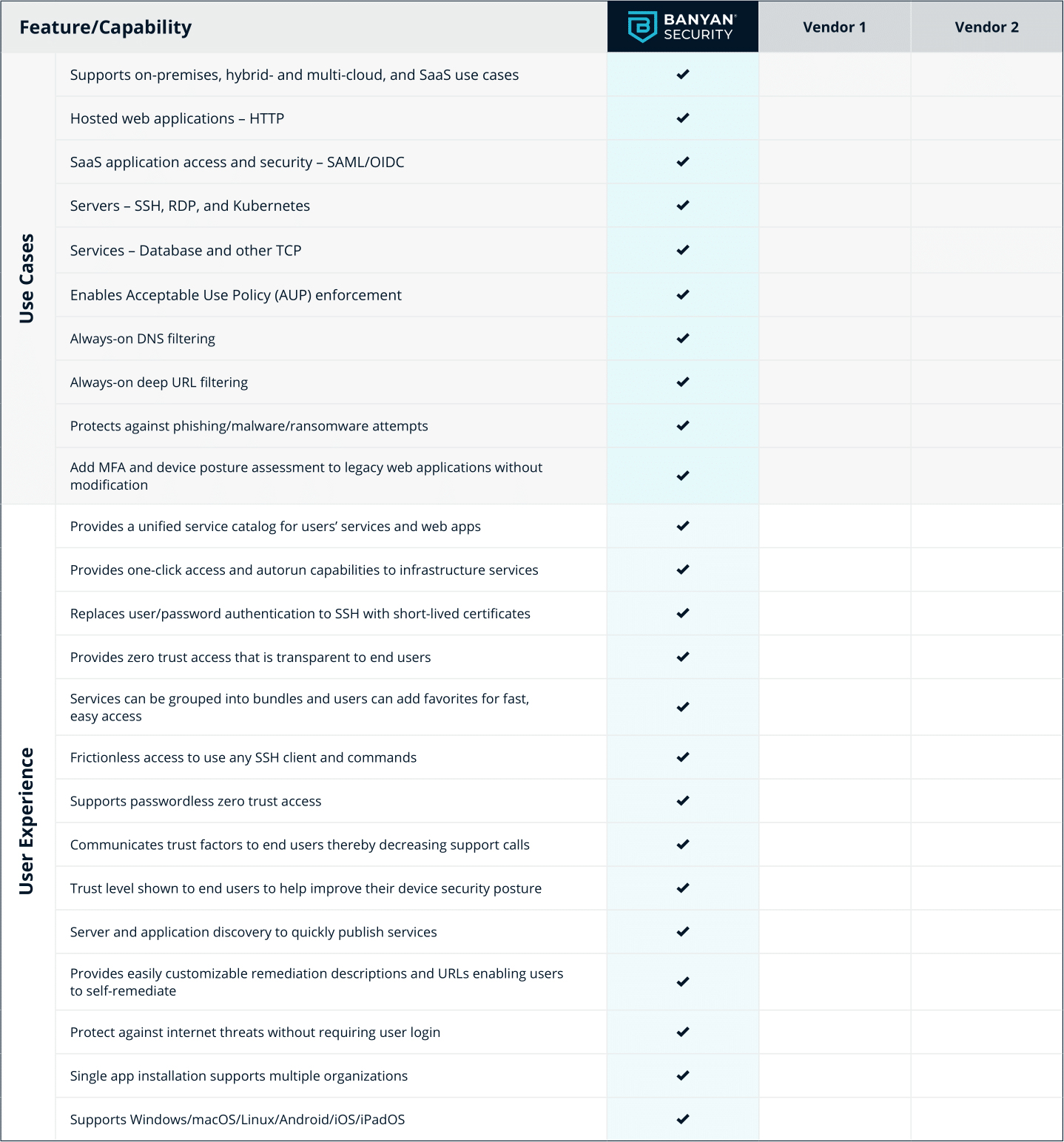
Security Service Edge (SSE) Evaluation Checklist
Free for 30 Days
Simple, secure, & free!
Quickly provide your workforce secure access to corporate resources and infrastructure.
