Device trust has come a long way, and is evolving even faster, stimulated by integrations and vendors that are developing device-centric solutions. But it wasn’t always this way… in the early networking days, a device that didn’t have a user (for example, a printer) would be put on a segmented network that wasn’t even secured. Anyone could unplug the printer, connect their computer, and get access to the network.
A brief history of device trust
This quickly became the weakest link in the network, so functionality like Network Access Control (NAC) and protocols like 802.1x were introduced. MAC authentication (what Cisco calls “mac auth bypass”) used a MAC address as username and password. Sadly, companies that had thousands of phones, printers, and other devices would have to manually enter each device. This was not ideal and took forever, often resulting in incorrect entries. This was followed by automated profiling based on mac address OUI (organizationally unique identifier). OUIs would identify the device to allow them to be automatically added to specific VLANs.
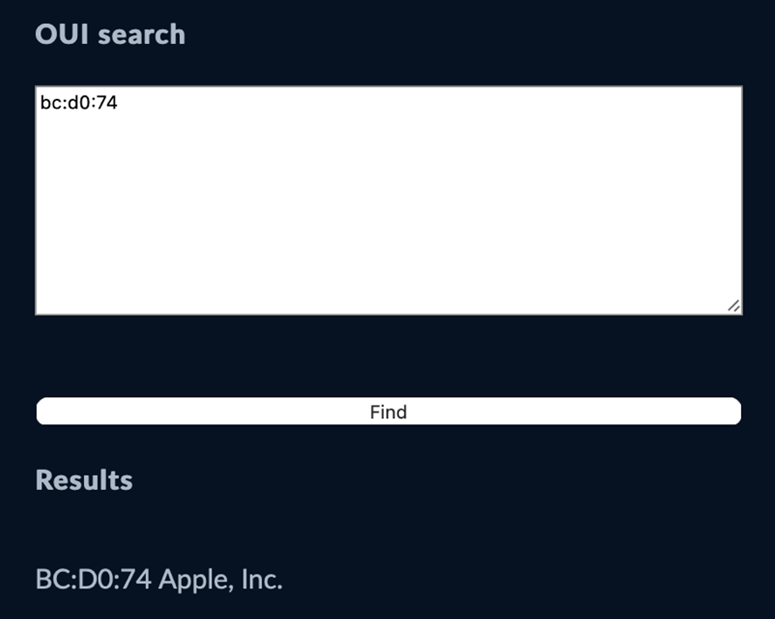
To quickly check out how OUI works, you can get the MAC address of the physical or Wi-Fi network interface and then check it against WireShark’s OUI lookup tool. Here’s an example of the (partial) MAC address of my MacBook:
Next on the scene: Internet of Things (IoT) and management server integration came along, and were useful to get extensive information on devices trying to connect to local networks, usually in manufacturing environments. As systems became more proprietary and didn’t support basic networking, they had management systems offering APIs or integration with systems that use standard protocols like RADIUS.
Both IoT and NAC protocols are helpful when dealing with on-premises and mostly fixed devices. So, what can be done for mobile and portable devices coming in from anywhere in the world?
So what is mobile device trust for?
Mobile device trust isn’t just for mobile devices like cellphones or tablets, but also for laptops. A solution should tie into mobile device management (MDM) and unified endpoint management (UEM) solutions that can be used to configure devices with zero-touch from the end user, as well as collect important device information that’s needed for certain types of compliance: how the device is configured, what applications are loaded on it, or location, for example.
Device identity is integral when creating a device trust policy. Device trust policies can be based on ownership type, such as corporate or customer-owned (in the case of BYOD). These policies can also be based on type (such as Apple or Android) or screen size, which may make connection types like RDP easier to use.
Device posture is just as important as identity. Device posture checks ensure that the device is in a state that the organization requires. This may include having the proper configuration, settings, and applications running. Device posture can also tie into endpoint detection and response (EDR) software for deeper inspection of traffic and applications which may detect malware and other unwanted software.
A word about UEBA
Knowing about the user on the device, the device itself, and the health state of the device is great, but a good user on a good device may still present a problem. That’s where User and Entity Behavior Analytics (UEBA) comes into the picture. Let’s take the example of discovering a company’s “business hours.” Most organizations may say business hours are Monday to Friday from 9am to 6pm, however, these business hours may not apply to software developers or devops folks that are working atypical hours pushing updates. The UEBA engine should create baselines for each user, and policies can be created to react when behavior is outside of the threshold of the learned behavior.
Having outdated device trust information is useless. Unlike other vendors that have lightweight device info, Banyan’s Device Trust is always-on; the effective changes to authorization based on device trust are real-time, happening almost instantly, resulting in the safest possible device-to-resource communication.
To learn more about how Banyan’s real-time Device Trust can help your organization deflect breaches, schedule a demo today.



