Ensuring Compliance When Your Employees Skirt the Rules
Shadow IT refers to the use of information technology (IT) systems, devices, software, applications, or services within an organization without explicit approval or oversight from the IT department or management. Shadow IT typically occurs when employees use their own devices or software to perform work-related tasks without the knowledge or consent of the IT department. This practice can lead to security vulnerabilities, compliance issues, and inefficiencies within an organization.
Protection Against Shadow IT
To protect against shadow IT, organizations can take several measures:
1. Educate and Communicate
Raise awareness among employees about the risks associated with shadow IT. Help them understand the importance of using approved IT systems and the potential consequences of using unauthorized applications.
2. Establish Clear Policies
Develop and communicate IT policies that clearly outline which tools, software, and applications are approved for use within the organization. Ensure these policies are easily accessible and understandable for all employees.
3. Monitor Network Traffic
Employ network monitoring tools that can identify and track the use of unauthorized applications or devices within the organization’s network. This can help detect instances of shadow IT.
4. Provide Approved Alternatives
Offer employees approved and secure alternatives to the unauthorized applications or tools they might be using. Ensure that these alternatives are user-friendly and meet the needs of the employees.
5. Implement Security Measures
Strengthen the overall cybersecurity measures by using firewalls, encryption, and access controls to protect against potential security threats that could arise from the use of unauthorized software or devices.
6. Regular Audits and Reviews
Conduct periodic audits or reviews to identify any unauthorized IT usage within the organization. This can help in understanding the extent of shadow IT and taking appropriate measures to address it.
7. Encourage Feedback
Foster an environment where employees feel comfortable providing feedback about the tools they need. This could help in identifying gaps and understanding why employees turn to shadow IT.
8. Collaborate with Departments
Work closely with different departments to understand their specific needs and requirements. This collaboration can help in providing suitable IT solutions and reducing the likelihood of employees resorting to shadow IT.
Combat Shadow IT with Banyan Security
By employing a combination of these measures, organizations can better manage and mitigate the risks associated with shadow IT while also ensuring that employees have access to the tools they need to be productive in their roles.
Banyan Security’s Public and Private Resource Discovery features make it super easy for admins to quickly see which sanctioned and unsanctioned applications are being used and start protecting against them.
Naturally, the next question would be, so what can we do once we see unsanctioned applications? Step one may be to simply block the entire category of applications, say AI tools, while doing some more investigation. You may find that a specific tool needs to be allow-listed while blocking the rest of the sites in the category.
The next step will be to ensure that all authentication of sanctioned applications is done via your identity provider (IdP), which also validates devices using Banyan Security’s Device Trust. It may be necessary to redirect all traffic over a Service Tunnel for a limited time to further monitor where your users are going, resulting in even more applications being discovered. Your users will not need to do anything different, which makes it even better.
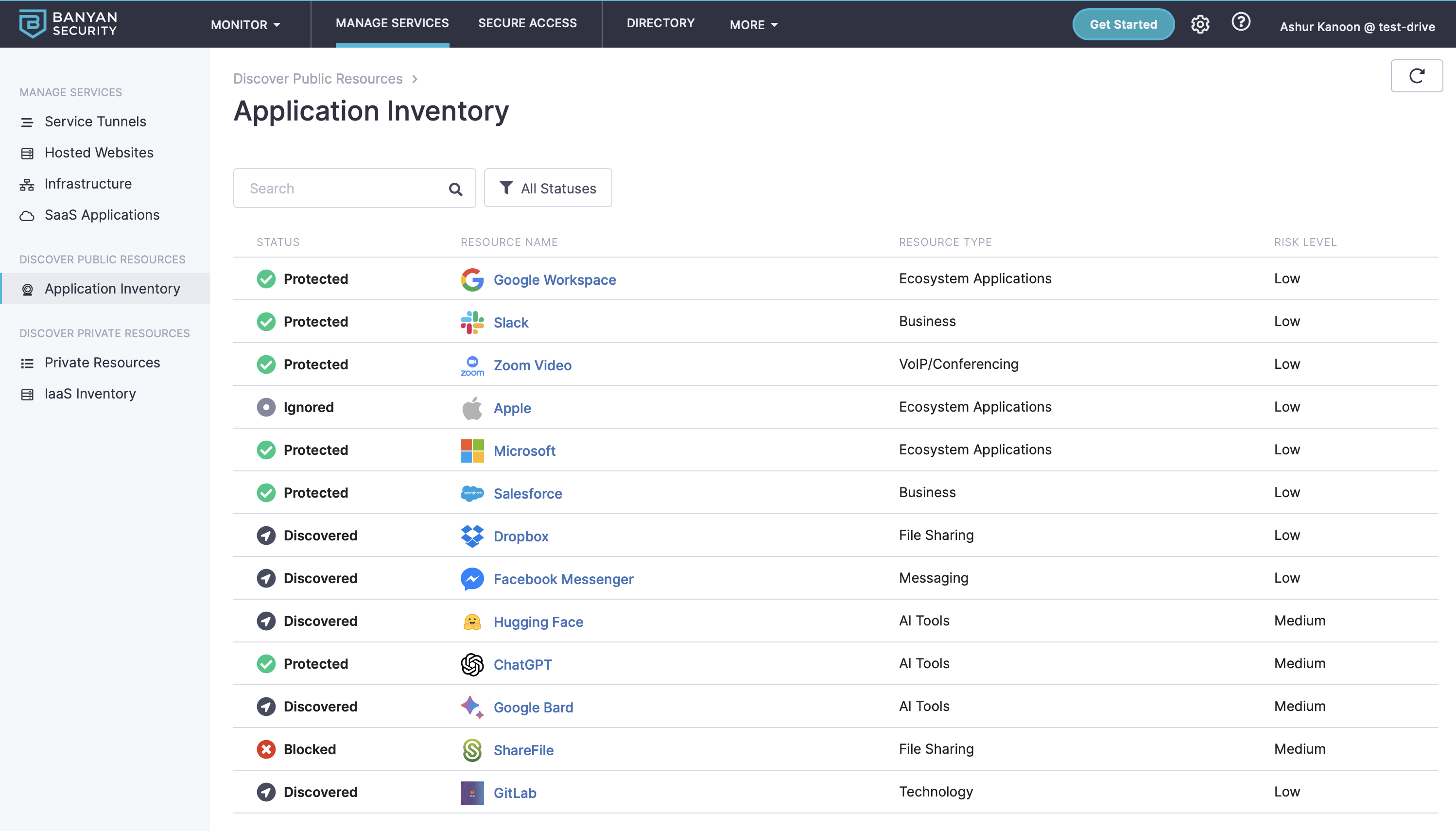
Will employees try other methods to use unsanctioned apps? They may. Will you be able to find these unsanctioned apps? Possibly. As an IT or IS leader, you may have to look at corporate expenses submitted by users or groups to discover shady behavior. If your expense system has the “Software/Licenses” category, you may be able to identify shadow IT that’s being used and expensed on machines that aren’t registered or corporate-owned. While this may be an extreme case, it is still possible. To help reduce corporate risk, it may be a step you consider doing.
To learn more about Public and Private Resource Discovery, visit https://docs.banyansecurity.io/docs/visibility-logging/service-tunnel-discovery/



